Tips to Prevent Sybil Attacks from a Web3 Perspective
How to Prevent Sybil Attacks from a Web3 Perspective
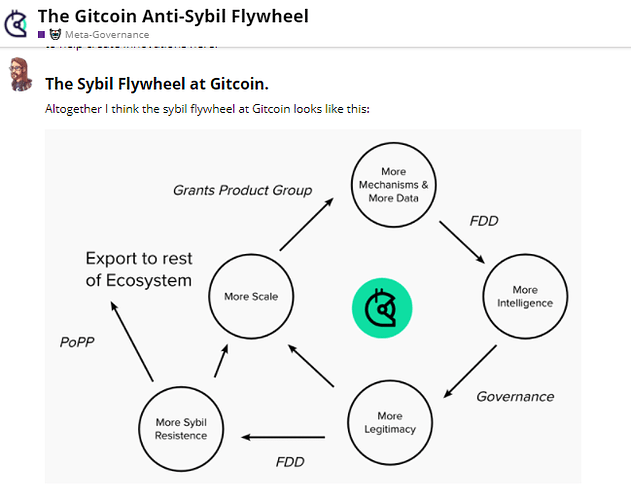
Today, in the context of decentralized apps, a Sybil attack is a scenario in which an attacker poses as many users as possible in order to infiltrate a system and succeed in secretly abusing it. In other words, it’s when the attacker creates multiple fake identities in order to have a more realistic chance at success. It’s a lot easier to play multiple identities on the web than it is on the blockchain. The Sybil attack is when you create multiple identities on different websites, and interact with those websites under different identities. That being said, a Sybil attack against a decentralized application (dApp) is no different than a Sybil attack against a centralized one. A decentralized application that supports a Sybil attack would require the attacker to have fake identities on different nodes in order to achieve their goal. In this article, we will discuss how to prevent Sybil attacks from a web3 perspective.
Ethereum and Web3: A Match Made in Heaven
Decentralized applications are able to host their own token, and if we think about it, it’s the perfect way to build a Sybil attack. By the same token, a decentralized application is able to detect a Sybil attack and shut it down before it can even begin.
Neutrality and on-chain identity
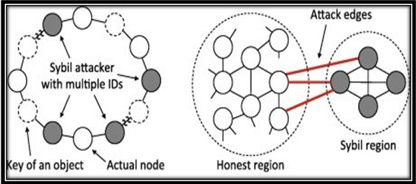
One of the most important concepts in web3 security is neutrality. It means that the network should not favor certain identities over others. If an application, for example, decides to reward Bob for interacting with Alice and rewarding Eve for interacting with Eve, then the network is biased and this would be a Sybil attack. Achieving neutrality on the Ethereum network is a very challenging problem. There are various proposals for the use of off-chain identity authorities and on-chain identification, but none have been proven to work yet.
Final words
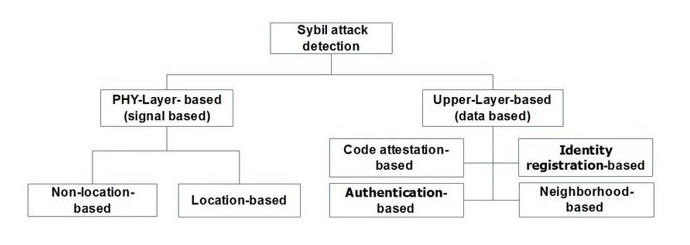
In summary, Sybil attacks are a lot easier on the centralized internet compared to decentralized one. They are still possible, but harder to achieve on the decentralized Web3. The best way to prevent them is by having a network that protects users from Sybil attacks. This means creating a network that encourages neutral interactions, and punishing those that violate the network rules. That being said, a Sybil attack against a decentralized application is no different than a Sybil attack against a centralized one. A decentralized application that supports a Sybil attack would require the attacker to have fake identities on different nodes in order to achieve their goal. In the future, we might see new decentralized applications that create an environment that is more friendly to Sybil attacks. For now, we can protect ourselves by using decentralized applications and exploring the capabilities of the decentralized web.