How to Prevent Sybil Attacks: A Guide to Preventing Fraud in the Web3 Ecosystem
Sybil attacks happen when an attacker creates multiple user accounts with the specific intention of targeting specific individuals. From there, they can use those profiles to carry out fraudulent activities with those accounts. These attacks are difficult to prevent, as the definition of a “sybil” is a user who poses as someone else. However, there are some steps that anyone who operates a decentralized application can take to prevent sybil attacks in the context of their ecosystem. In this article, we’ll explore what sybil attacks are, how they work, and how you can prevent them in the web3 ecosystem.
What is a Sybil Attack?
A sybil attack is the act of creating multiple user accounts with the specific intention of targeting specific individuals. From there, they can use those profiles to carry out fraudulent activities with those accounts. Fraudulent users with multiple accounts can easily deceive other users through impersonation. This happens by creating an account that is similar to another person’s account in some way, such as their username, bio, past activity, or other details. This impersonation can be done to mislead other users and can have a significant negative impact on the community. From there, they can abuse their power by impersonating other users or accounts to carry out fraudulent activities. This includes ICO scams, spamming, or any other fraudulent activity. Even outside the context of fraud, multiple accounts can also create trust issues for other users who might not be comfortable sharing their identity with someone else.
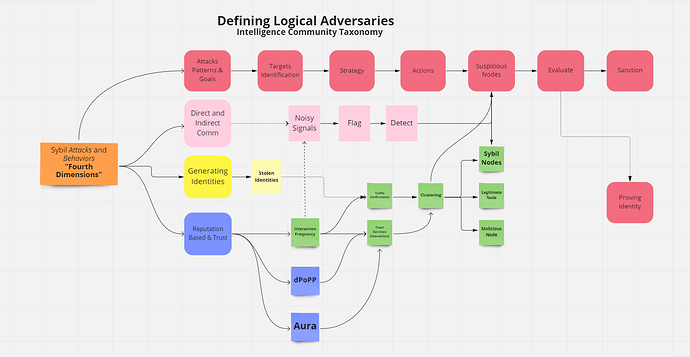
Defining Logical Adversaries, Intelligence Community Taxonomy
How Sybil Attacks Work in the Web3 Ecosystem
A sybil attack happens when a user creates multiple accounts with the specific intention of targeting specific individuals. From there, they can use those profiles to carry out fraudulent activities with those accounts and attacks your organization. While sybil attacks happen in centralized ecosystems, they are especially problematic in the decentralized web3 ecosystem. However, the same measures that prevent them in other ecosystems also apply. The main difference is that you’re operating a decentralized application, which makes it even more important to prevent sybil attacks. It can be difficult to distinguish between legitimate users, especially since many people will have a vested interest in joining your ecosystem. To prevent sybil attacks in the web3 ecosystem, you should strive to provide strong user authentication and a clear signoff process. This way, you can know who’s actually using your App/dApp and which accounts belong to which users.
How to Prevent Sybil Attacks in the Web3 Ecosystem
A strong user authentication along with a clear signoff process, strong user authentication is one of the most important ways to prevent sybil attacks in the web3 ecosystem. With strong user authentication, you can ensure that only the user making the signoff approves a transaction. This is especially important in decentralized applications, but it also applies to centralized applications as well. There are a few different ways to implement strong user authentication on your App/dApp. Firstly, you can require user accounts to be verified using a personal identity attach (PIE). Secondly, you can implement a centralized or decentralized approach to KYC. Thirdly you can use decentralized software applications like dPoPP AURA (Both in construction)
Centralized Approach to KYC
The most straightforward way to prevent sybil attacks in the web3 ecosystem is to implement a centralized approach to KYC. You can do this by verifying users with a government-issued form of identity, such as a passport or driver’s license. While this may seem like a straightforward solution, there are a few important considerations to keep in mind. Firstly, it’s important to verify users quickly. We’ve seen in the past that fraudsters have been able to create fake accounts with verified profiles. This gives them quick access to your App/dApp and can result in fraudulent activity quickly. Secondly, it’s important to verify on the blockchain. The only way to guarantee that you’re verifying users’ identity on the blockchain is to verify them on the blockchain as well.
Decentralized Approach to KYC
Along with a centralized approach, a decentralized approach to KYC allows you to verify users directly on the blockchain. This can help prevent sybil attacks by verifying the real-world identity of a user. This is especially important for decentralized applications, as users may not have a government-issued form of identity. You should also consider using a reputation management system (RMS) to help prevent false positives.
Projects to Protect From Sybil Attacks
The projects in this section are the most promising to prevent sybil attacks in the web3 ecosystem. We’ve reviewed their projects in depth and found that they have a good chance of preventing sybil attacks in the web3 ecosystem.
Furthermore - Gnosis. Gnosis is constructing a decentralized prediction market that uses decentralized applications as a protocol. This will make it much harder for scammers to target specific users through Gnosis.
IPFS. (Blockchain Dev) IPFS content addressing enables you to store large files off-chain and put immutable, permanent links in transactions — timestamping and securing content without having to put the data itself on-chain. IPFS is a distributed content delivery network that could greatly reduce the amount of spam in the Gnosis prediction market. This could prevent scammers from targeting specific users on IPFS, which would prevent sybil attacks.
Conclusion
In this article, we explored what a sybil attack is and how it works in the web3 ecosystem. We also covered how to prevent sybil attacks and explored potential projects that you can use to protect your users. These attacks are difficult to prevent, as the definition of a “sybil” is a user who poses as someone else. However, there are some steps that anyone who operates a decentralized application can take to prevent sybil attacks in the context of their ecosystem.